Google has announced its plans to enhance the security of its Google Workspace products, such as Gmail and Drive, using artificial intelligence (AI). While emphasizing that Google Workspace has never had an exploit, the company is committed to staying ahead of security issues as businesses increasingly move to the cloud. The upcoming updates will include improvements to the zero trust model and data loss prevention capabilities. For instance, Google aims to automate data classification and labeling using AI capabilities, allowing for the application of appropriate risk-based controls. Additionally, enhanced controls in Gmail will prevent users from inadvertently attaching sensitive data, while context-aware controls will be added to Drive to define criteria for sharing sensitive information. Moreover, AI will be employed to detect data breaches and suspicious actions within the platform. Google’s focus on data sovereignty will also introduce client-side encryption for mobile versions of Gmail, Calendar, and Meet, ensuring customers have complete control over their data. These advancements and others are currently in development and will be rolled out in the near future. While pricing details have not been disclosed, it is expected that the availability of certain features may depend on the type of account and may require additional payment.

Enhancements for Zero Trust Model
Google Workspace is constantly working to stay ahead of security issues, and one area they are focusing on is enhancing their zero trust model. Zero trust is a cloud security model that removes implicit trust and enforces strict identity authentication and authorization. Google is combining the concept of zero trust with data loss prevention (DLP) to further enhance security.
One of the new capabilities Google is adding is the automatic classification and labeling of sensitive data within Drive. Using AI capabilities, Google Workspace will continuously classify and label sensitive data, and apply appropriate risk-based controls. This will help organizations better manage and protect their sensitive information.
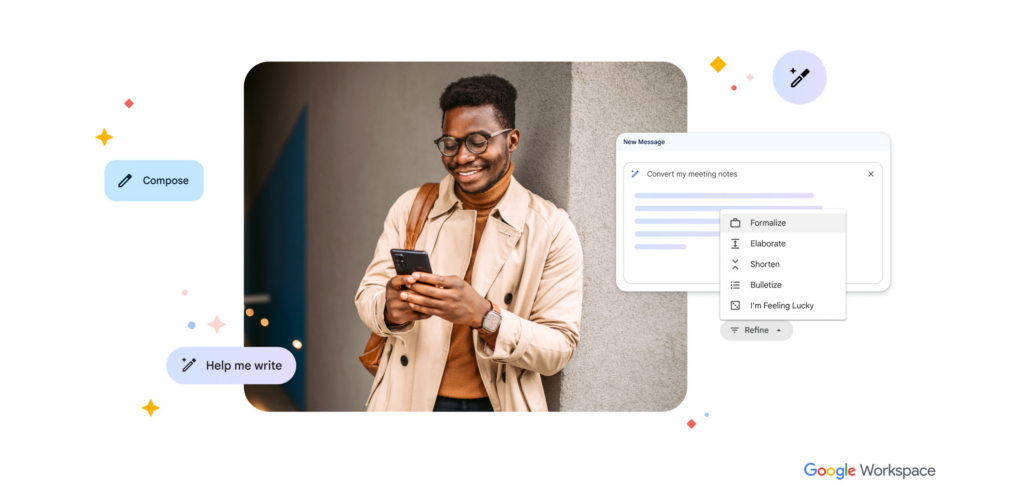
Additionally, Google is introducing enhanced DLP controls for Gmail. These controls will allow administrators to prevent users from inadvertently attaching sensitive data, especially when it appears in unexpected places. For example, if a customer support email contains sensitive data, administrators can disable download or prevent copy and paste on those documents, ensuring that sensitive information doesn’t end up in the wrong hands.
Automatic Classification and Labeling of Sensitive Data
With the automatic classification and labeling of sensitive data in Drive, Google is leveraging AI capabilities to simplify the process of managing and protecting sensitive information. This feature automatically classifies and labels sensitive data, making it easier for organizations to apply appropriate risk-based controls. By continuously monitoring and categorizing data, organizations can stay on top of data security and ensure that sensitive information is properly protected.
This enhancement not only saves time and resources, but it also adds an extra layer of security by automating the classification and labeling process. This means that organizations can focus on other important tasks while still maintaining control over their sensitive data.

Applying Risk-Based Controls
The concept of risk-based controls is essential in maintaining a strong security posture. Google is taking this concept into account by allowing organizations to apply risk-based controls to their sensitive data. With the combination of zero trust and data loss prevention (DLP), administrators can establish and enforce policies to mitigate the risks associated with sensitive data.
By implementing risk-based controls, organizations can define the level of access and permissions for different types of data. This ensures that only authorized individuals can access and interact with sensitive information. By taking a proactive approach to risk management, organizations can greatly reduce the chances of data breaches and unauthorized access.
Enhanced DLP Controls for Gmail
Gmail is one of the most widely used email platforms, and with that comes the need for robust data loss prevention (DLP) controls. Google recognizes this and is enhancing Gmail with additional DLP features to prevent the inadvertent attachment of sensitive data.
Administrators can now set up controls that prevent users from attaching sensitive data in unexpected places. This is particularly useful in customer support scenarios where sensitive information may accidentally be included in an email. By disabling download or copy and paste options for certain documents, administrators can ensure that sensitive data remains secure and cannot be easily shared or leaked.
These enhancements to Gmail’s DLP controls give administrators more control over the security of sensitive data and help prevent data breaches and compliance violations.
Strengthening Security Policies
In addition to preventing the inadvertent attachment of sensitive data, Google is also helping organizations strengthen their security policies within Gmail. Administrators now have the ability to customize security settings to meet their specific needs and raise the bar on their security measures.
For example, administrators can disable certain actions such as downloading or printing attachments, preventing unauthorized individuals from accessing sensitive information. By customizing security policies, organizations can ensure that their data remains secure and confidential.
These enhancements to Gmail’s security policies give organizations greater flexibility and control over their sensitive data, allowing them to tailor their security measures to align with their unique requirements.
Context-Aware Controls in Drive
Google Workspace is introducing context-aware controls in Drive, allowing administrators to set criteria for sharing sensitive data. This feature takes into account the location of the user’s device as one of the criteria for sharing sensitive data.
By setting specific device location requirements, organizations can ensure that sensitive data is only shared with authorized individuals who are in approved locations. This mitigates the risk of accidental sharing or unauthorized access to sensitive information.
Context-aware controls in Drive provide an extra layer of security by considering the context in which data is shared, enhancing overall data protection and reducing the likelihood of data breaches.
Setting Criteria for Sharing Sensitive Data
With the new context-aware controls in Drive, administrators have the ability to set specific criteria for sharing sensitive data. These criteria can include device location, ensuring that data is only shared with authorized users in approved locations.
By setting these criteria, organizations can limit the risk of accidental sharing of sensitive data. This is particularly important in scenarios where employees may be working remotely or using different devices. With context-aware controls, organizations can maintain control over their sensitive data, even in a distributed work environment.
Considering Device Location
Device location is an important factor to consider when it comes to data security. By incorporating device location into the criteria for sharing sensitive data, organizations can ensure that data remains secure and is only accessible to authorized individuals in approved locations.
This feature is especially useful when dealing with remote or mobile employees who may be accessing sensitive data from different locations. By leveraging device location as a control criterion, organizations can maintain a higher level of security and prevent unauthorized access to sensitive information.

AI-Powered Log Data Analysis
Google is harnessing the power of AI to analyze log data for data breaches and behavioral anomalies. This advanced analytics capability helps administrators proactively identify and respond to security threats.
By analyzing log data, AI can detect patterns and anomalies that may indicate a data breach or unauthorized access. This allows organizations to take immediate action and prevent further damage. AI-powered log data analysis provides an additional layer of security by continuously monitoring for any suspicious activities that could compromise data integrity.
Detecting Data Breaches and Behavioral Anomalies
AI-powered log data analysis is an invaluable tool for detecting data breaches and identifying behavioral anomalies. By analyzing log data, AI can identify patterns and anomalies that may indicate unauthorized access or unusual behavior.
This proactive approach allows organizations to quickly respond to potential security threats and mitigate the impact of data breaches. By leveraging AI-powered log data analysis, organizations can stay one step ahead of malicious actors and protect their sensitive data.
Identifying Suspicious Actions in Gmail
In addition to detecting data breaches and behavioral anomalies, AI-powered log data analysis is also capable of identifying suspicious actions in Gmail. This includes actions that may indicate that a hacker has gained unauthorized access to an account.
By continuously monitoring Gmail activity, AI can identify unusual actions or patterns that could be indicative of a security breach. This allows organizations to take immediate action and secure compromised accounts before any further damage is done.
AI-powered log data analysis in Gmail provides an added layer of security, helping organizations prevent unauthorized access and ensuring the integrity of their email communications.
Client-Side Encryption for Mobile Versions
Google Workspace is extending client-side encryption to mobile versions of Gmail, Calendar, and Meet. This enhancement ensures that sensitive data remains secure, even when accessed from mobile devices.
Client-side encryption means that encryption keys are controlled by the customer, not Google. This provides an extra layer of security, as Google cannot see the encrypted data. Even if requested by law enforcement, Google cannot share the encrypted information.
Extending client-side encryption to mobile versions of Google Workspace tools ensures that sensitive data is protected no matter where it is accessed from. This is especially important in today’s mobile-first work environment, where employees are increasingly relying on mobile devices for work-related tasks.
Extending Encryption to Gmail, Calendar, and Meet
By extending client-side encryption to mobile versions of Gmail, Calendar, and Meet, Google Workspace is ensuring that sensitive data remains secure across all platforms. Whether accessing emails, managing calendars, or participating in virtual meetings, users can have peace of mind knowing that their data is encrypted and protected.
This enhancement aligns with Google’s commitment to data security and privacy. By placing encryption keys in the hands of the customer, Google can guarantee that sensitive information remains confidential and protected from unauthorized access.
Customer Control over Encryption Keys
Key to client-side encryption is the fact that customers have complete control over encryption keys. Encryption keys are generated by the customer and used to encrypt the data before it is transmitted or stored. Because Google does not have access to the encryption keys, they cannot decrypt the data.
This gives customers full control over their sensitive data and ensures that it remains private and secure. It also provides an additional layer of protection against unauthorized access or data breaches.
By giving customers control over encryption keys, Google is empowering organizations to take ownership of their data security and prioritize privacy.
Data Residency and Processing
Google Workspace recognizes the importance of data residency and processing for organizations. To address this, Google is introducing the ability for customers to choose the location of their data residency and data processing.
Data residency refers to the physical location where data is stored, while data processing location refers to the geographical region where data is processed. By allowing customers to choose these locations, Google is giving organizations more control over their data and ensuring compliance with local regulations and privacy requirements.
Choosing Data Residency Location
Organizations now have the option to choose the location where their data resides. This is particularly important for companies that must comply with specific data residency regulations. By choosing the data residency location, organizations can ensure that their data remains within their desired jurisdiction.
Google’s commitment to data residency allows organizations to have peace of mind knowing that their sensitive data is stored and managed in compliance with their specific requirements.
Selecting Data Processing Location
In addition to choosing the data residency location, Google is also giving organizations the ability to select the data processing location. This ensures that data is processed in accordance with local privacy and security regulations.
By allowing organizations to choose the data processing location, Google gives them greater control over their data and ensures that it is handled in a manner that aligns with their specific requirements.
Upcoming Releases
Google Workspace has several upcoming releases planned to further enhance the security features and capabilities of their products. These releases will be rolled out in the coming months, and customers can look forward to the following new features:
- Release Timeline for New Features: Google will provide a timeline for the release of new security features and enhancements. This will enable organizations to plan and prepare for the implementation of these features in their Google Workspace environment.
- Pricing Details and Account Types: Google will provide more information on the pricing structure for the new security features. Different account types may have different pricing options, and organizations can choose the option that best suits their budget and security requirements.
These upcoming releases demonstrate Google’s commitment to continuously improving and evolving their security offerings. By staying ahead of emerging threats and addressing customer needs, Google Workspace ensures that organizations can trust in the security and reliability of their platform.
In conclusion, Google is actively working to enhance the security capabilities of Google Workspace to address the evolving needs and challenges of modern organizations. By combining the principles of zero trust with data loss prevention, Google is providing organizations with powerful tools to protect their sensitive data.
Through automatic classification and labeling of sensitive data, enhanced DLP controls in Gmail, and context-aware controls in Drive, Google is empowering administrators to enforce strict security policies and prevent data breaches.
The integration of AI-powered log data analysis further strengthens security measures by detecting data breaches, identifying behavioral anomalies, and recognizing suspicious actions in Gmail.
Extending client-side encryption to mobile versions of Gmail, Calendar, and Meet ensures that sensitive data remains secure, even on the go. By giving customers control over encryption keys, Google ensures that data remains private and protected.
The ability to choose data residency and processing locations gives organizations a level of control and compliance that is essential in today’s global business landscape.
With upcoming releases, Google continues to innovate and evolve their security features, providing organizations with the tools and capabilities they need to confidently protect their sensitive data.









![Frugal Budget For Christmas [Idy On Fire]](https://investitin.com/wp-content/uploads/2018/12/586-Arctcle-100x70.jpg)
